Credentials for thousands of open source projects free for the taking—again!
[ad_1]

Getty Visuals
A provider that helps open up source developers create and exam computer software is leaking thousands of authentication tokens and other stability-delicate tricks. A lot of of these leaks allow hackers to access the private accounts of developers on Github, Docker, AWS, and other code repositories, security experts mentioned in a new report.
The availability of the 3rd-party developer qualifications from Travis CI has been an ongoing dilemma since at least 2015. At that time, stability vulnerability company HackerOne claimed that a Github account it used experienced been compromised when the services exposed an accessibility token for one particular of the HackerOne developers. A comparable leak offered itself yet again in 2019 and yet again final yr.
The tokens give any person with entry to them the potential to read or modify the code stored in repositories that distribute an untold quantity of ongoing software program applications and code libraries. The potential to get unauthorized obtain to such assignments opens the likelihood of provide chain attacks, in which threat actors tamper with malware ahead of it truly is dispersed to end users. The attackers can leverage their means to tamper with the application to target massive figures of tasks that rely on the app in manufacturing servers.
Irrespective of this getting a regarded security problem, the leaks have ongoing, scientists in the Nautilus crew at the Aqua Stability company are reporting. A sequence of two batches of info the researchers accessed using the Travis CI programming interface yielded 4.28 million and 770 million logs from 2013 by May 2022. Immediately after sampling a compact share of the data, the scientists discovered what they consider are 73,000 tokens, strategies, and numerous credentials.
“These accessibility keys and credentials are joined to well-liked cloud company vendors, such as GitHub, AWS, and Docker Hub,” Aqua Protection said. “Attackers can use this delicate details to initiate huge cyberattacks and to go laterally in the cloud. Any individual who has at any time made use of Travis CI is perhaps uncovered, so we advise rotating your keys right away.”
Travis CI is a company of an more and more common practice recognised as ongoing integration. Frequently abbreviated as CI, it automates the process of setting up and screening every single code modify that has been committed. For just about every modify, the code is routinely created, analyzed, and merged into a shared repository. Given the level of obtain CI wants to perform effectively, the environments typically retailer accessibility tokens and other techniques that present privileged accessibility to sensitive components inside the cloud account.
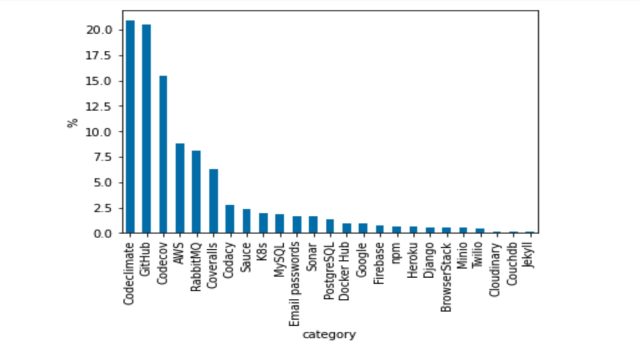
The accessibility tokens found by Aqua Stability involved private accounts of a wide variety of repositories, including Github, AWS, and Docker.

Aqua Stability
Illustrations of obtain tokens that were being exposed incorporate:
- Accessibility tokens to GitHub that might make it possible for privileged obtain to code repositories
- AWS accessibility keys
- Sets of qualifications, usually an e mail or username and password, which enable access to databases this kind of as MySQL and PostgreSQL
- Docker Hub passwords, which could guide to account takeover if MFA (multi-variable authentication) is not activated
The next graph reveals the breakdown:
Aqua Security
Aqua Stability scientists additional:
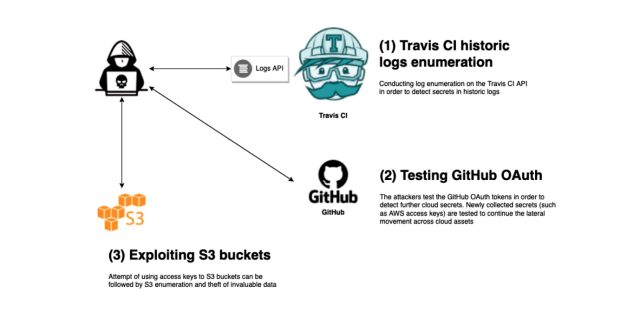
We uncovered countless numbers of GitHub OAuth tokens. It is protected to think that at least 10-20% of them are stay. Specifically those that were discovered in the latest logs. We simulated in our cloud lab a lateral movement situation, which is centered on this first entry scenario:
1. Extraction of a GitHub OAuth token by way of exposed Travis CI logs.
2. Discovery of sensitive info (i.e., AWS access keys) in private code repositories employing the exposed token.
3. Lateral movement makes an attempt with the AWS access keys in AWS S3 bucket company.
4. Cloud storage item discovery by way of bucket enumeration.
5. Details exfiltration from the target’s S3 to attacker’s S3.
Aqua Security
Travis CI associates failed to quickly react to an e-mail trying to get remark for this publish. Presented the recurring nature of this exposure, builders should really proactively rotate obtain tokens and other credentials periodically. They ought to also on a regular basis scan their code artifacts to make sure they will not have credentials. Aqua Safety has additional guidance in its article.
[ad_2]
Resource connection