A closer look at Valorant’s always-on anti-cheat system

Vanguard has two main components: a traditional scanning service that boots up when the game does, and a device driver that loads at system start. The driver runs the entire time your PC is on, even if you’re not playing Valorant. Players even have to reboot their computers before starting the game for the first time, in order to properly install Vanguard’s kernel-mode component.
“The driver itself doesn’t do any of the scanning or communicate with the network or anything like that,” Chamberlain said. “It’s there to make sure that from the start of your computer booting until when the game starts, the system hasn’t been compromised or tampered with. It does this by starting up before any cheats could be loaded on your system. And then as new drivers or modules load on your computer, it checks them for security vulnerabilities. If it finds them, it doesn’t let them load. This is unusual.”
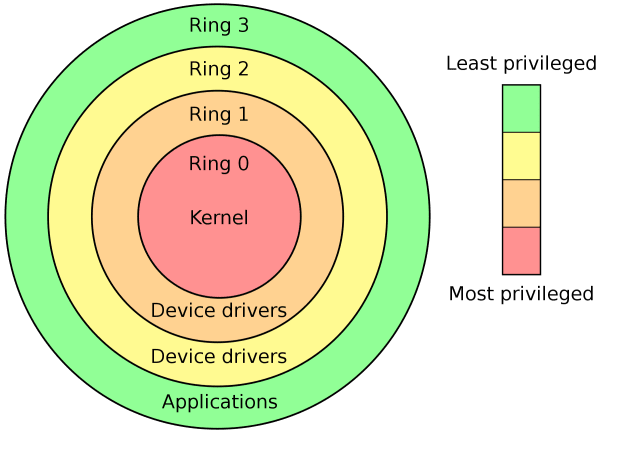
Operating in the kernel, or ring 0, means Vanguard has access to every bit of a computer’s hardware. It’s the most privileged level of a PC, reserved for only the most trusted bits of the operating system. From ring 0, attackers can modify game memory, crash an entire system or access files from other users on the computer. And hackers don’t even need to be involved for the driver to cause problems — Vanguard is crashing some computers as it blocks otherwise harmless software from operating properly. We’re talking like blue-screen-of-death failures.
Hertzsprung at English Wikipedia
“The other thing is that there are certain parts of the operating system that need to be able read and write to your game memory,” Chamberlain said. “They start when the computer starts as well. A common technique for getting a cheat into a game is to hijack one of these system components. Since the system components are running the whole time, you can’t verify their integrity unless you have a component that’s running the whole time. And that’s most of what the kernel driver does.”
Chamberlain presents the system as a bubble of security shielding the entire computer from cheating software, but Rashid said Vanguard has a blind spot when it comes to ring 0 attacks. He said, “Vanguard’s premise is that they can use a kernel driver to detect a specific kind of cheat injection that happens in ring 3, in user mode. But when cheat developers also move their cheats into the kernel, they can modify game memory in a way that Vanguard’s driver cannot detect. This technique is already used to bypass existing anti-cheat mechanisms.”
This analysis is playing out in real-time, as cheaters have been active in Valorant since week one. Of course, no anti-cheat system is completely fool-proof and Riot expected attacks, even with Vanguard’s extra layer of protection.

Riot Games
The problem, according to Rashid and other experts, is that Vanguard isn’t just blind to some kernel attacks — it’s actively inviting cheaters and hackers to target a computer’s most privileged level. Chamberlain agreed that this concern is valid, but he said most existing malware has no interest in ring 0.
“If I’m running a driver and I get a virus on my PC, the virus can exploit that security vulnerability in the driver to also run in ring 0, in the kernel, and then do anything in the kernel,” Chamberlain said. “This is actually relatively rare because most malware doesn’t have any interest in kernel-level access to a computer because all the things that are valuable on your computer are accessible from user mode. The things that I want protected like my browsing history or my credit cards, and all the fanfiction that I’m writing, that’s all accessible to anything on my computer. You don’t need a kernel driver for that.”
Operating systems use exploit mitigations to protect user-mode applications from attacks, but this security blanket doesn’t cover kernel code. Cheat developers and hackers can still use security vulnerabilities in Vanguard and other trusted drivers to target the kernel and install software there, bypassing security certificate requirements entirely.